4 Simple Home and Work Cyber Safety Tips
Upon arrival at the Riverside County Sheriff’s Department for cyber security training by a division of Homeland Security, I asked for a password to access wireless internet but my request was denied. I was surprised by the lack of Internet access for a sophisticated technology course but as the class progressed, the reason became clear.
Even the most sophisticated technology is susceptible to human error. In the blink of an eye, an innocent mistake such as allowing access to a computer network or inserting an infected storage device into a computer’s USB drive can shut down a network or severely interrupt functionality. To reduce such risks, a family, organization or business can create customized guidelines that are easy to understand and to follow. Everyone with access to technology should be made aware of the guidelines and should also demonstrate the ability to follow and abide by them.
4 basic steps to help with cyber security:
1. Install software and application updates promptly on all devices and keep virus protection current
Updates and patches may include security corrections so upgrade promptly after receiving notifications. This applies to all devices including cell phones, tablets, computers and laptops.
2. Do not give others access to your work or home network
My children’s friends often use our home wireless network for computer games. I trust them, however, allowing access provides opportunity to invade our network to steal information, introduce a virus or to get into another form of technological mischief. The same applies to a work environment. A network can be interrupted and breaches and loss of important information can be extensive. It’s logical that law enforcement would restrict access to its network but perhaps not as obvious that we need to be careful on home networks which run the same risks of malware installation and related negative consequences.
- The first level of protection for home and work computer networks is a strong password that is changed regularly and that is difficult to guess. The second level is keeping that password private and secure!
- Suspicious behavior or cyber threats should be reported to appropriate people at work or to the cyber division of a local police department.
- When non-employee internet access is required at work, access to a separate network that is not connected to critical business systems is recommended.
- Password protected guest internet access is suggested at home with selective access and regular changing of passwords. For more information read, 5 Important Steps for Home Cyber Security
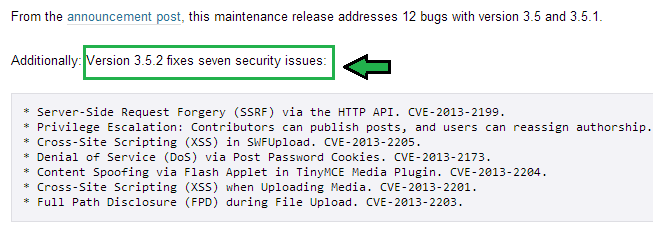
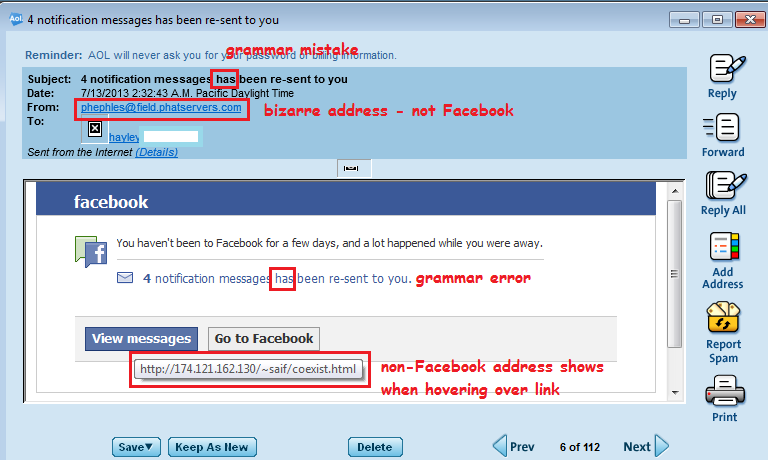
3. Don’t become a phishing victim at home, work or elsewhere
Phishing scams appear to come from trusted sources such as friends, banks, businesses, social network sites or even coworkers and bosses. Clicking on disguised links directs victims to infected sites or tricks them into revealing personal information which can result in money loss and identity theft. Phishing scams can even allow individual computers to be taken over and used as weapons for attacks on other targets in DDoS (Denial of Service) attacks. These attacks can result in websites becoming inaccessible to real customers because of a sudden and huge surge in fake traffic and many financial intuitions have been affected in recent months.
For more phishing information, see How to Avoid Phishing Scams and I just became a Phishing Fool
4. Be careful when installing software or inserting anything into computers, cell phones or other devices
USB drives, memory sticks, pen drives, CD’s and cell phones are examples of devices that can install malware on your technology.
- If you find a CD or USB drive, don’t try to see what’s on it out of curiosity or to return it to its owner. These items can be left out intentionally to lure victims into infecting their own technology.
- Disable auto-run features on computers and other devices to avoid malware from being automatically installed upon insertion of a disk or USB drive.
- Be wary of free and promotional USB drives as they can be a source of malware and infection.
- To reduce potential infections, limit installation of outside software at work to qualified individuals.
- Prevent cell phone charging on computers since cell phones can infect a computer with malware.
The overused cliché, “a chain is as strong as it’s weakest link” is right on target when it comes to cyber security.
It only takes a single household member or employee who doesn’t understand the guidelines to break down a previously secure system. At work, every employee with technology access from janitors to CEO’s should be included in awareness and education of technology guidelines. At home, every family and household member should be included in multiple discussions to insure guidelines are clear to all. Household members that are unable to understand and follow the guidelines should only use Technology and the Internet with competent supervision.
There are many ways to run into cyber trouble but negative repercussions can be reduced with education and information sharing. Some of the most interesting tips I’ve gotten have come from unexpected and surprising sources, including my own children and people in presentation audiences. I hope you are pleasantly surprised by the knowledge you acquire from listening and talking to others and when you learn something helpful or important, please remember to share it!
Until next time … Stay Cyber Safe!

















Thanks for sharing these helpful safety tips. These tips will really help people to make sure that they will not become the victim due to lack of cyber and home security.
You’re welcome, Daniel. I see we have safety in common – yours being physical safety (locksmith) and mine being cyber safety. Thanks for reading and commenting.
People leave flashdrives out and about to mess with people? pretty twisted!
It’s more than messing with people. While pure malice is a possibility, the other reason is for identity theft. Once malware is installed on your device, the criminal has a way to access confidential information such as passwords used to log into banking information. Sad, but true.