How to protect yourself from FedEx, UPS, USPS and Amazon scams

Delivery Service and Amazon Scams
Watch out for dangerous Amazon, FedEx, UPS, USPS emails AND text messages that appear to be from these businesses but they are not! Many people are falling prey to these scams because vast numbers of consumers take advantage of the convenience and price savings of online ordering and they are mistaking fake delivery alerts for legitimate ones. Falling for one of these can cause multiple issues including having money wired directly out of your bank account. If money is wired out of your bank account because you did something to allow it to happen versus the bank being hacked, you may not get that money back. In order to protect yourself it’s helpful to understand why so many people are being infected, how to protect yourself and what to do in the event you get infected.
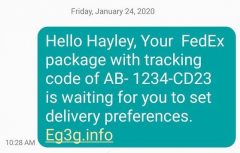
Example of a FedEx Scam Text
Why are many consumers falling for Amazon, FedEx, UPS and USPS scams?
- Many scam emails and texts aren’t riddled with as many errors as they used to have and they look legitimate.
- We already get text alerts and emails regarding the many orders we place so a scam text or email is not as out of place as it may have been in the past.
- We’re often distracted or inundated with so many texts or emails that we may not take the time to carefully analyze a text or email before clicking on a link or opening an email.
What can happen if you click on a malicious link or open a malicious email ?
Once infected your sensitive information including online login information for everything from your bank accounts to your social media accounts can be collected and duplicated by a perpetrator who can then use those logins for a variety of mischief.
- Your devices can be taken over and used to launch attacks against you and against others in a variety of ways.
- You can find yourself dealing with ransomware, annoying popups and adware.
- Your devices can become functionally challenging and slow to use, possibly even unusable.
- Your social media accounts can be used to wreak all sorts of havoc.
- In addition to clicking on links and opening malicious emails you can unknowingly become compromised by going to a legitimate website that is infected or by “drive-by downloads” and malicious files you downloaded yourself.
- A “drive-by download” can be installed on your device when clicking on a pop-up window with information that misleads you such as a fraudulent error message, by viewing an email or by browsing a website. You may not know you did something to install it and anti-virus software may not detect it either.
- A legitimate website can suddenly have a drive-by download that infects your device when you visit that site.
How can you protect yourself against malicious links, downloads and websites?
- Install security software on all of your devices. It may not protect you completely but it will usually warn you before you try to go to a malicious website and it will prevent known drive-by downloads.
- Insure your mobile phone is protected since most people are using these for email, texts and to access the Internet.
- Keep all device software up to date especially your operating system.
- Don’t install codecs (device or software that is used to compress or decompress a digital media file, such as a video or song) unless you’re absolutely positive that they’re safe.
- Delete suspicious or spam-like emails without opening them especially if they contain attachments or images and are from unknown senders.
- Prevent images from showing up via email settings. You can release that setting on a specific email when you determine it is safe.
- Evaluate every link before you click on it. When in doubt contact the person who sent you the email before clicking or go directly to a website instead of using the link.
- If your gut alerts you to any suspicion, go with it.
- If a website you go to asks for permission to install something or looks like it is automatically doing so, close out of that site and run your security software immediately.
What specific steps should you take if you suspect you may be infected by malware or a virus?
- Immediately disconnect from the internet to minimize the risk of providing sensitive information and to prevent other devices on your network from getting infected.
- Unplug if you’re using an ethernet cord.
- Turn off WIFI and disable Internet access using data.
- Backup your files. Focus on sensitive or irreplaceable files if you don’t know how to do a full backup.
- Run a complete system scan and ignore messages to connect to the Internet. Follow instructions regarding quarantine and restarting your device.
- If you do not have security software on your device, install on a clean device and transfer it over using a USB drive or other portable storage device. Next, install it on your problematic device and ignore prompts to connect to the internet. Once the scan is complete, follow the program’s recommendations. Ideally run two different anti-virus programs to insure removal of malware.
- Change your login information for all online accounts, preferably on a different device to be safe. (Only use your existing device after confirming malware is fully removed.)
- Changing usernames and passwords will provide more protection when that is possible.
- Avoid using the same username and password for multiple accounts as this makes it easier to hack you.
- Use two-factor authentication when available.
- This provides additional security by requiring you to reconfirm your identity and also notifies you if anyone tries to log into your accounts which allows you to do something about it.
While FedEx, USPS, UPS and Amazon scans are currently making news headlines they are by no means the only scams to watch for. Prevention is always better than dealing with a cure so why not take easy precautions such as having virus protection on all devices before you run into a problem and by knowing what else to do immediately should you accidentally become infected?
Until next time, … Stay Cyber Safe!






Thank you. I will look into it. I hope all is well with you. I miss seeing your pretty face.
Hi Hayley,
Thanks for the always helpful information. My Norton 360 is about to expire. Do you have nay suggestions for other antiviruses besides McAfee. I wasn’t crazy about them but that was years ago. Thanks for any input, and you can email me directly.
You’re welcome Lonnie!
I used Norton many years ago and found it slowed down my computer and caused software conflicts for me – it may be better now, I don’t know. I use bitdefender and like it a lot. It’s quarantined a few infections for me on my macs over the years and seems to be doing a good job so far.
🙂 Hayley