Taking Control of Privacy
There is no doubt there are aspects of privacy that are out of our control, but as discussed in the last post called Privacy we Cannot Control, there are solid options for reducing the impact of privacy invasion. Today’s post reminds us there are many ways to take control of our privacy – it’s not time to mourn the death of privacy just yet. Heads up, highlighted sentences are links to detailed articles but only click on links when you want more information or getting through this article may become tedious.
Remove your personal information from the Internet:
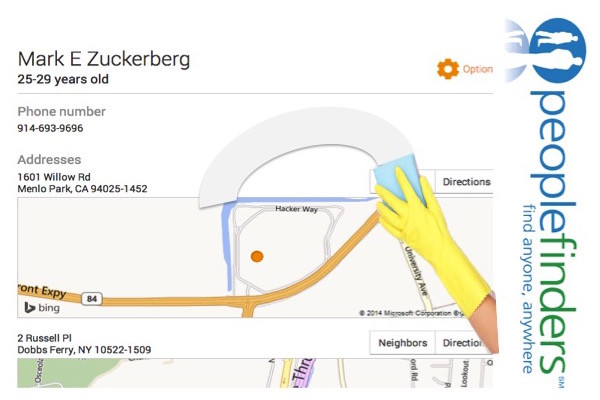
- Remove yourself from popular search engines and make your private information more difficult to locate online.
Minimize repercussions of breaches and privacy invasion:
- Check bank, credit card statements and credit reports regularly to identify issues promptly.
- If you suffer a privacy breach, notify pertinent parties immediately and review all records and activity frequently thereafter. You can also get assistance from a reputation management company.
Be cautious communicating about confidential information:
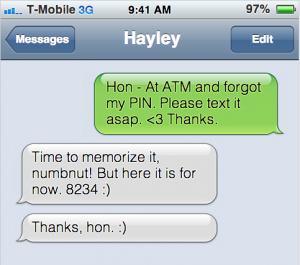
- Do not text or email confidential data (login info, passwords, account numbers, credit card numbers, pins, social security numbers). Getting a written password request from a family member could mean someone else has their device and you could accidentally provide a criminal access to a bank account. Private emails may be viewed in a variety of circumstances so avoid using sensitive data in email.
- Encrypt sensitive information at home and work.
- Bank and shop on secure networks only. Be wary of public Wi-Fi.
- Log out after using public computers. To avoid leaving trails surf incognito and delete cookies before logging off.
- Have you noticed people talk loudly on mobile phones? Eavesdroppers may be listening. Maintain privacy when discussing confidential information on any telephone.
- Shred documents with sensitive/confidential information. (Medical, financial and business information that can be pieced together to provide private details.)
Be careful with social media and email:
- Enjoy benefits of social media but understand risks too.
- Understand and enable privacy settings for social media and apps.
- Assume someone always has a camera and avoid doing anything that could harm you if photos are shared.
- Understand rights you give up when an app takes actions on your behalf.
- Understand the anatomy of a phishing scam and avoid clicking on malicious links. Beware of bitlys (shortened links) too.
- Work and personal emails carry the risk of being hacked into. Work emails may be legally viewed by others.
- Be aware of social media photo and status updates and understand which pose risks to you, your family, your friends or your business.
- Unless you have good reason, avoid sharing real time location of yourself, family and friends as it can be used for robbery or stalking purposes.
Be aware of tracking:
- Know when you are being tracked and if it’s helpful or harmful. For example, if you don’t mind sharing your shopping habits, use a reward card for checkout and coupon discounts or to be contacted regarding recalls. (I was thankful for a recent market recall notification on chicken I had purchased but not yet eaten.)
- Recognize that tracking creates a profile of your spending habits and when privacy policy allows, retailers may share your information with others. Discounts are great, but how would you feel if you began to receive baby food and diaper coupons after confidentially purchasing a pregnancy test?
- When entering online contests, you may relinquish privacy by providing an email address or access to your social media or contact list. Is the slim chance of winning a contest worth the privacy invasion?
Provide personal information to trusted organizations only:
- Opt-out of anything that makes you uncomfortable, including tracking cookies, apps, privacy policies and sharing of data.
- Sever relationships with people and organizations that betray your trust. However, there are times when the best protection and intentions fail. Determine whether to continue your relationship with these entities based on how they respond and protect you after a mishap!
And last but not least, a basic and critical yet often ignored suggestion …
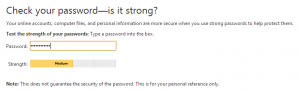
Use exceptionally good passwords:
- Use strong and unique password protection on all devices including computers, tablets and cell phones.
- Use strong and unique passwords for each site and change them often.
Let’s fight for our privacy! Together we can do it!
Until next time,… Stay Cyber Safe.













Leave a Reply
Want to join the discussion?Feel free to contribute!